Adobe rolled out a new Adobe Commerce Security Update (APSB25-94) for both Adobe Commerce and Magento Open Source. It fixes several critical and important issues that could allow unauthorized access or remote code execution.
These vulnerabilities can let attackers take over a store or leak customer data. Most ecommerce setups have complex connections, custom modules, ERPs, or third-party plugins, which make them harder to protect if even one gap stays open. One unpatched issue can slow down operations or cause data loss across linked systems.
This update is part of Adobe’s normal patch cycle, but the severity makes it a high-priority release. Stores managing large catalogs, payment data, or admin-level integrations should apply it right away to avoid unnecessary risk.
ON THIS PAGE
What is in the Adobe Commerce (APSB25-94)

Adobe Commerce (APSB25-94) went live on October 14, 2025. It addresses several high-risk and moderate security flaws that could allow attackers to gain extra privileges, run unauthorized code, or bypass system protections. Adobe says there are no known exploits right now, but that can change once the update details are public.
In the past year, Adobe has increased its release pace. Updates like APSB25-71 and APSB25-88 were pushed out only weeks apart because new threats kept surfacing. Hackers keep an eye on these official updates to spot stores that haven’t applied them yet.
This release signals that Adobe found real issues that need fixing without delay. Anyone still on older versions should assume they’re exposed until they apply the patch.
What is the Risk if You Miss Patching
Unpatched stores face multiple risks. A single exploit can give attackers control over admin accounts or direct access to the database. They can modify checkout scripts, steal payment details, or install malware that hides behind legitimate processes.
This isn’t just a backend problem. Compromised code often leads to broken features, redirects, or slower page performance. These directly affect conversion rates and customer trust.
Fixing a security breach is more expensive than applying a patch. You’d have to thoroughly track all the loose ends, clean up, audit the flaws, and may even have to disclose it to customers or partners. However, applying Adobe Commerce security patches is quicker.
What’s Included in the New Adobe Commerce Security Patches
Adobe hasn’t listed the full CVE details in the summary, but APSB25-94 covers both critical and important vulnerabilities across supported versions, from 2.4.4 to 2.4.7. The fixes strengthen input validation, access control, and protection against remote code execution.
These are the areas most frequently exploited in ecommerce attacks. They impact how admin permissions, API endpoints, and custom modules handle incoming requests.
This update applies to all environments, including Adobe Commerce Cloud, on-premise setups, and Magento Open Source. Even if your site seems stable, running without these patches leaves you exposed. Every environment, including dev, staging, and production, needs to be updated.
Why Regular Patching is Important
Security updates like Adobe Commerce (APSB25-94) are not optional maintenance. They protect against vulnerabilities that directly affect store operations and data safety.
Attackers often use automated scanners to find outdated Adobe Commerce versions. Once detected, they deploy payloads that exploit known flaws. Regular patching blocks that entry point.
It also helps maintain performance and system stability. Older versions accumulate compatibility issues, especially when third-party extensions are involved. By keeping up with Adobe’s release cycle, you reduce integration issues, security warnings, and downtime.
Patching regularly also improves compliance with data protection standards such as PCI-DSS. These frameworks require all ecommerce systems to apply security updates promptly.

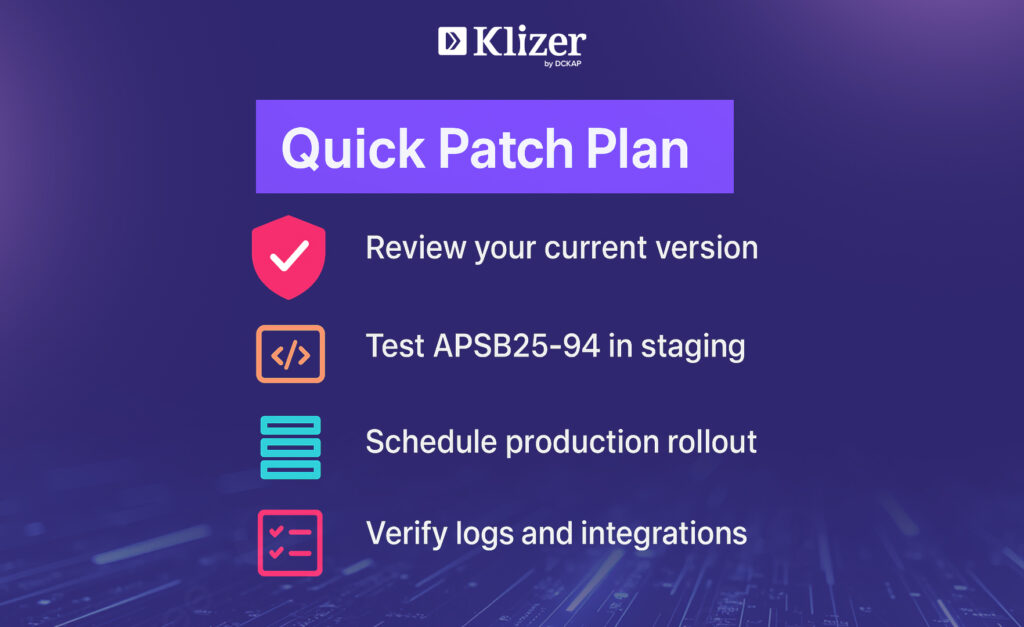
Action Plan for Applying Adobe Commerce (APSB25-94)
Step 1 — Audit All Environments
Start by checking which version your production and staging environments are running. Identify all extensions and integrations that might be affected. Having a clear inventory avoids compatibility surprises after patching.
Step 2 — Test in Staging First
Apply the Adobe Commerce Security Update in a staging environment. Test core processes such as checkout, product imports, and API connections. This helps confirm that critical functions continue to work after the update.
Step 3 — Schedule Deployment
Choose a deployment window that causes minimal disruption. Inform all relevant teams in advance. Always back up your site before applying any patch.
Step 4 — Verify After Deployment
Once patched, review your system logs. Look for new admin activity, login attempts, or errors in integrations. Run a malware scan and verify file integrity. This confirms that your update was applied cleanly and your store remains secure.
Step 5 — Establish a Regular Patch Routine
Adobe has issued multiple security bulletins this year — APSB25-26, APSB25-71, APSB25-88, and now APSB25-94. These come frequently enough that patching should be part of your monthly or quarterly maintenance process. Document every patch cycle and test outcome for compliance records.
How Adobe Connects Security with Performance
A well-maintained store runs faster and is easier to monitor. Many security issues begin as performance anomalies — sudden slowdowns, failed API calls, or caching errors. These symptoms often trace back to outdated code or unpatched modules.
By staying current with Adobe Commerce security patches, you reduce performance overhead and keep the platform stable. This ensures consistent response times and protects SEO rankings, especially during high-traffic periods.
Regular updates also simplify upgrades. When you’re already on the latest secure version, adopting the next feature release becomes easier. You avoid version jumps and emergency fixes that can interrupt business operations.
Conclusion
The Adobe Commerce (APSB25-94) release reinforces the need for consistent security management. Adobe’s recent frequency of updates shows how quickly new risks emerge.
If you’re managing an ecommerce platform, install this patch without delay. Treat every Adobe Commerce Security Update as part of normal operations, not a one-time event.
Keeping your store patched is not just about avoiding breaches. It preserves stability, compliance, and long-term performance. Regular patching is a sign of a reliable ecommerce operation, one that’s built to handle both security demands and business growth.
If you are an Adobe Commerce store owner and need help to ensure regular security and compliance for your custom ecommerce website, reach out to our Adobe Commerce development experts now!










